Threat Modeling API Gateways: A New Target for Threat Actors?
By David Fiser and Alfredo Oliveira
Application Programming Interfaces (APIs) enable functionality by integrating different software components and facilitating data exchange. APIs enable application communication by allowing microservices to use a standardized interface without needing to disclose internal implementations. APIs can be found in our daily lives — for example, browsing social media platforms, such as Facebook, X (formerly Twitter), or Instagram, requires calling API endpoints in the background.
In terms of usage and adoption, nearly 90% of developers are using APIs. And according to Gartner, the number of third-party API usage will triple by 2025. As they’re used now more than ever, securing APIs and their gateways becomes increasingly challenging. An unsecured endpoint is like a gate that’s left inadvertently open, letting unwelcome gate crashers and burglars in the form of cybercriminals enter to steal sensitive data.
The use of APIs also proliferated with the increased adoption of microservices and cloud-based applications. Because every modern application will interact with an API at some point, APIs could and should be further shielded from attacks, and they should be aggregated under an API gateway, which serves as an entry point to the API world. API gateways are often marketed as a tool for increasing security and tackling API security and visibility issues.
Why is it important to secure APIs and API gateways? In this article, we will focus on API gateway functions and risks, the advantages of API gateways in hybrid and multi-cloud environments, and common API security risks and best practices.
API gateway functions and risks
API gateways have the following functions:
- Authorization/authentication. API gateways implement strong authentication mechanisms, including multifactor authentication, to verify the identity of users and applications. Additionally, these gateways use authorization methods, such as role-based access control (RBAC) or access control lists, to define what actions users are allowed to perform on specific resources.
- Routing. A basic function of an API gateway is routing API requests to corresponding back-end systems. This can be done as a simple reverse proxy or, in more complex scenarios, with additional policies capable of modifying requests, replies, or even adding authorization.
- Offloading. Offloading refers to the process of delegating tasks such as Secure Sockets Layer (SSL) handling, request caching, and response transformations to the API gateway, rather than handling them within the applications themselves. This can significantly reduce the load on individual services and improve overall system performance.
- Transport Layer Security (TLS) termination. TLS termination at the API gateway means that this becomes the endpoint for TLS encryption, decrypting requests before passing them to back-end services.
- Aggregation. API gateways can aggregate responses from multiple back-end services and deliver a unified response to the client, which simplifies client-side logic and reduces the number of requests needed.
- Single point of access. This centralization can simplify security management, serving as a single entry point for all API requests. Thus, the API gateway simplifies the API ecosystem for clients.
Each of these gateway functions has its own associated risks. In this article, we will focus on user-managed on-premises and hybrid API gateways. These gateways still have support for cloud services but are not marketed as a service for cloud service providers (CSPs). They also usually provide more configuration options and use cases.
However, with bigger power comes bigger responsibility — and the likelihood of making a mistake and introducing a misconfiguration increases with the use of API gateways. The main security concern starts with authorization and TLS termination.
We’ll start off with an example of a bad authorization policy using an API gateway. A secret (such as an API key) is needed for accessing the endpoint, but if the request gets forwarded to the actual back-end service without any authorization required, the back end authorizes the request by default.
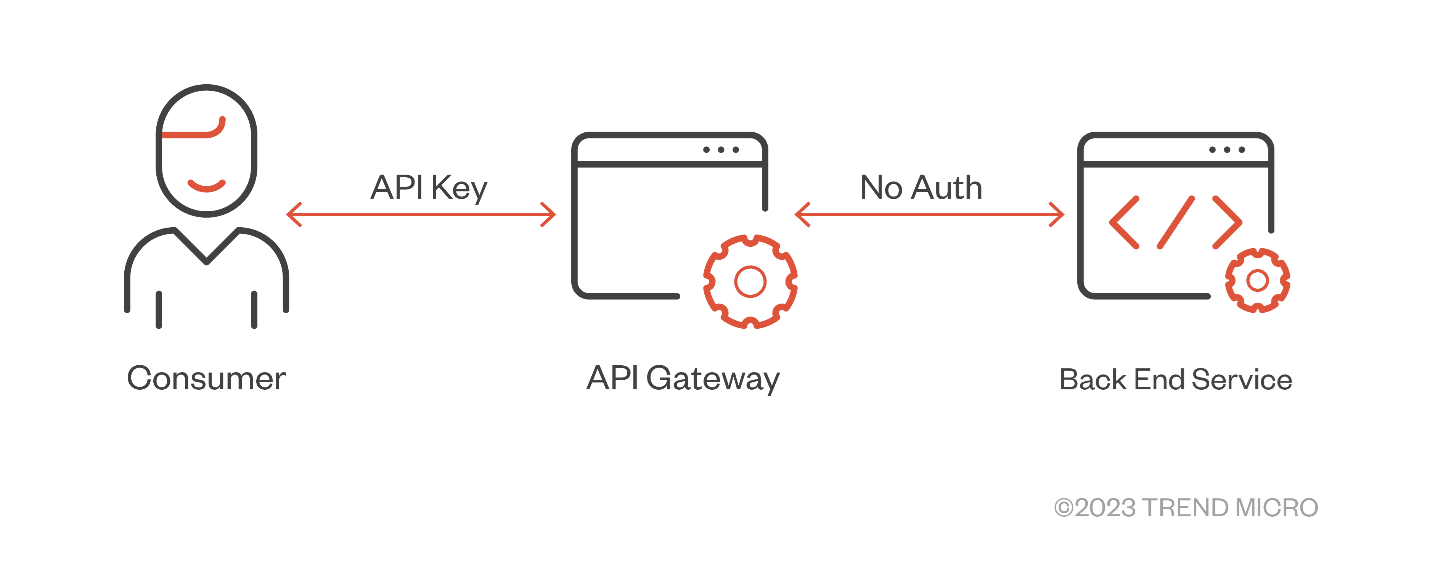
Figure 1. An example of a bad authorization policy using API gateway
This means that whoever has access to the back-end service inside the internal network does not need any authentication at all. This setup makes the service vulnerable to server-side request forgery (SSRF) attacks. In case a service within the internal reachable network is compromised, the service inadvertently gives free access to malicious actors, allowing them to potentially carry out attacks.
When it comes to TLS termination, one of its benefits is the reduction of the performance overhead needed to send encrypted requests and decrypt them on the other end. However, authorization secrets are sent in plain text with TLS termination. This could allow for attacker interception, which is especially prevalent in on-premises workloads.
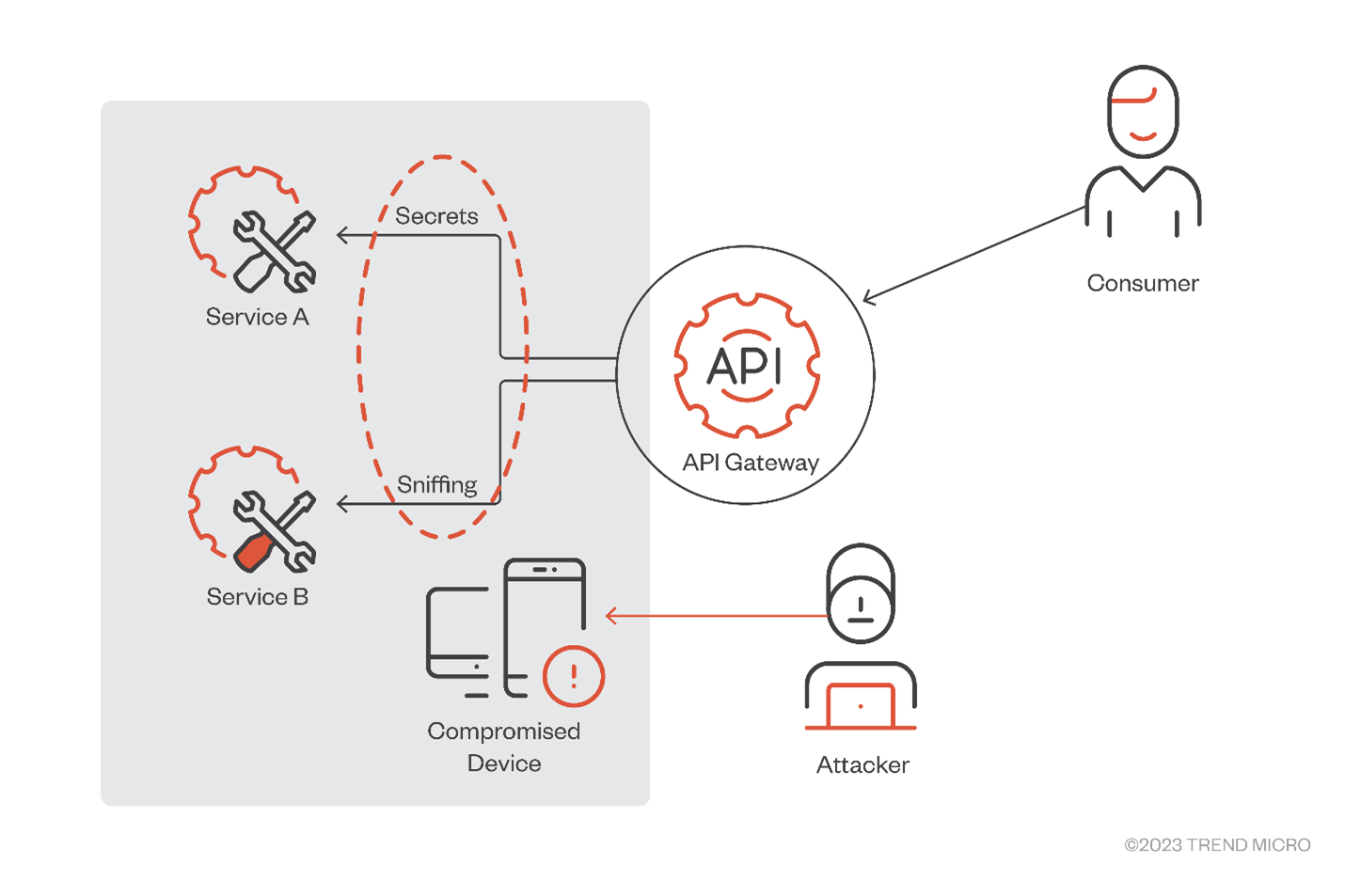
Figure 2. An attacker can sniff API secrets in a compromised device inside a private network when TLS termination is used
This is why access control, TLS, and proper secrets storage are key elements in API gateway security.
API gateway advantages in hybrid, multi-cloud environments
While API gateways can introduce security challenges, hybrid and multi-cloud environments can benefit from them significantly.
In such environments, applications and services are distributed across various cloud platforms and on-premises infrastructure. This distribution can create a complex web of interactions that can be tricky to manage and secure.
API gateways can simplify this complexity by serving as a single point of access for all API interactions, regardless of where the underlying services are hosted. This centralization enhances security by providing a unified platform for implementing security policies, including authentication, authorization, and encryption.
Moreover, API gateways can provide a consistent interface for all API interactions, making it easier to manage and monitor API usage across the entire hybrid or multi-cloud environment. This consistency can also simplify the process of adapting to changes in underlying services or migrating services between different platforms.
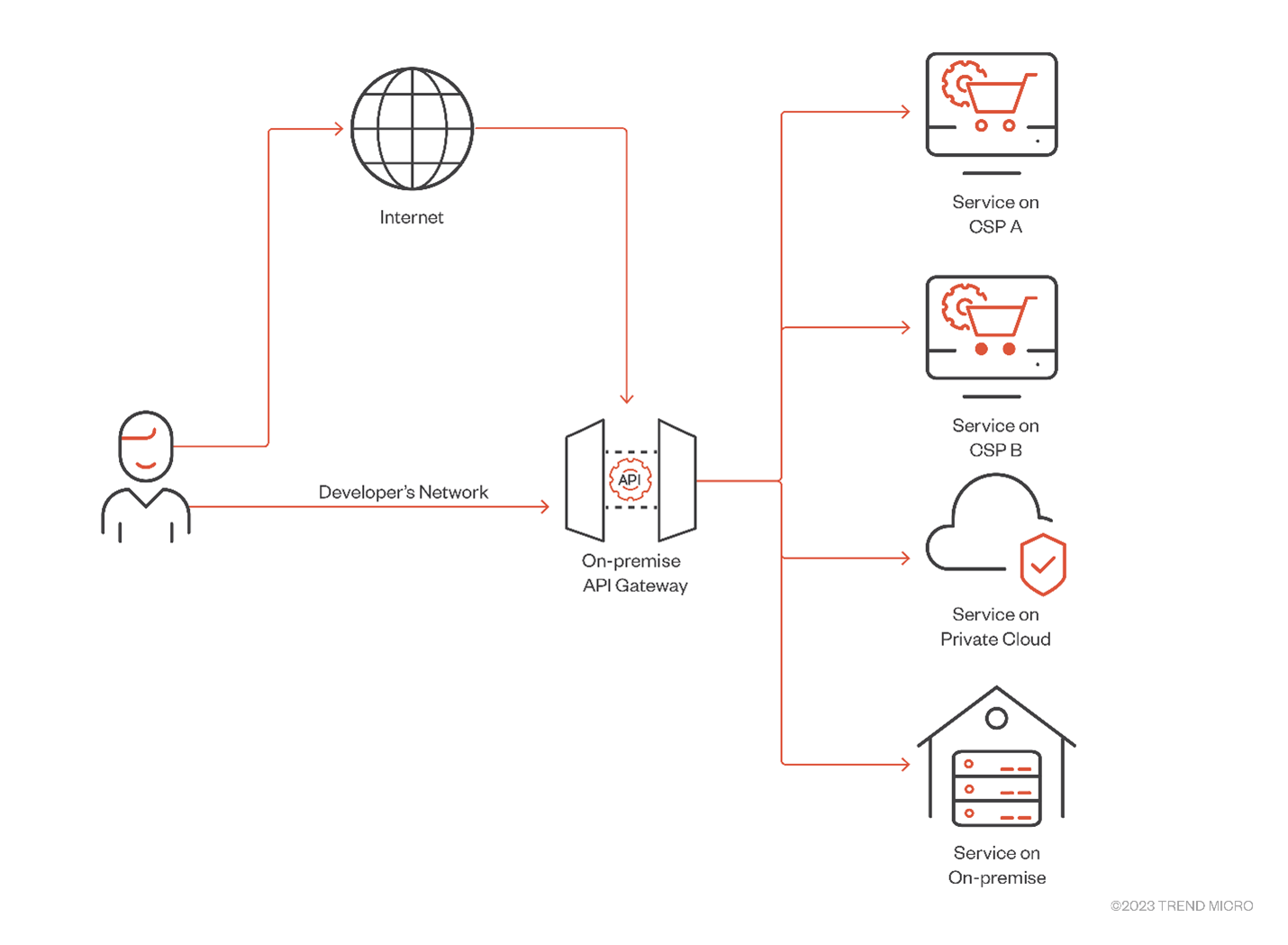
Figure 3. API gateway serving as single access point in a multi-cloud architecture
As with any technology, the key to taking advantage of these benefits while minimizing risks lies in proper configuration, vigilant monitoring, and adherence to security best practices. As it aggregates settings to access multiple environments including their secrets, when a single API gateway is compromised, it can lead to the compromise of multiple CSP and on-premises accounts.
API security challenges and best practices
While securing API gateways is vital, the importance of securing the APIs themselves should not be overlooked. The Open Web Application Security Project’s (OWASP) cites the top ten API security risks, such as broken object-level authorization, broken authentication, unrestricted resource, broken function-level authorization, server-side request forgery, security misconfiguration, and lack of protection from automated threats.
To further understand API security, let's delve deeper into other common API security challenges and their potential solutions.
- Inadequate rate limiting. Without proper rate limiting, APIs can be vulnerable to brute-force attacks where an attacker tries numerous credential combinations to gain unauthorized access to systems. To mitigate this risk, organizations should implement strict rate-limiting rules that curb the number of API calls a user can make within a certain timeframe.
- Insufficient data validation. APIs often interact with various data sources, which can introduce vulnerabilities if the data is not properly validated. Organizations should always validate client-side and server-side data to ensure it meets the necessary criteria and does not contain malicious code.
- Insecure direct object references (IDOR). This occurs when an API exposes a reference to an internal implementation object. An attacker can manipulate these references to gain unauthorized access to data. To prevent IDOR, organizations can benefit from using indirect object references and ensuring that proper authorization checks are in place.
- Lack of logging and monitoring. Without proper logging and monitoring, it can be difficult to detect and respond to API security incidents. Companies should implement comprehensive logging and real-time monitoring to identify unusual activity and promptly respond to potential security threats.
- Insecure API dependencies. APIs often rely on other APIs or software modules, which can introduce vulnerabilities if these dependencies are not secure. Teams handling APIs should regularly update and patch API dependencies to ensure that they do not contain known vulnerabilities.
- Lack of encryption. Data transmitted via APIs should always be encrypted to prevent interception. To avoid risk, it would be advantageous to use protocols like HTTPS and implement proper encryption methods to secure data in transit and at rest.
- Inadequate authentication and authorization: APIs should always verify users’ identity (authentication) and ensure that they have the necessary permissions to perform an action (authorization). Organizations should implement robust authentication mechanisms like OAuth and ensure proper authorization checks are in place for all API endpoints.
- Misconfigured cross-origin resource sharing (CORS). CORS is a mechanism that allows many resources, such as fonts and JavaScript, on a webpage to be requested from another domain outside of the domain from which the resource originated. Misconfigured CORS can allow unauthorized domains to access the API. To boost security, it pays to always configure CORS correctly and only allow trusted domains to interact with the API.
- Exposed sensitive data. APIs often handle sensitive data that can be exposed if not properly protected. Encrypting sensitive data and implementing proper access controls to prevent unauthorized access can help mitigate the risk of inadvertent data exposure.
- Lack of API versioning. Without proper versioning, changes to an API can break existing integrations and introduce vulnerabilities. Companies can benefit from implementing a robust versioning strategy to ensure backward compatibility and secure transitions among different API versions.
Conclusion
The world of APIs is vast and complex, with a myriad of potential security issues lurking beneath the surface. As the use of APIs continues to grow, so does the need for robust security measures. By understanding the common challenges and potential solutions, and by learning from past incidents, organizations can ensure the security of their APIs while maximizing their potential for innovation and growth.
API gateways offer significant benefits, especially in hybrid and multi-cloud environments. Through proper configuration, vigilant monitoring, and adherence to security best practices, organizations can make the most of API gateways’ benefits while avoiding security risks.
Moreover, the role of API gateways becomes even more critical in the context of hybrid and multi-cloud strategies. In such environments, applications and services are distributed across various cloud platforms and on-premises infrastructure. This raises the challenge of securing these complex and intertwined connections. API gateways can simplify the complexity by serving as a single point of access for all API interactions. This offers a unified platform for implementing security policies, which enhances security.
Ultimately, the security of an API is not just about the technology but also about people and processes. It requires a comprehensive approach that includes education, regular audits, and a culture of security awareness. By taking these steps, organizations can protect their APIs and the valuable data that they handle, ensuring their continued success in the digital age.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Threat Modeling API Gateways: A New Target for Threat Actors?
- Rising Security Weaknesses in the Automotive Industry and What It Can Do on the Road Ahead
- Ransomware Spotlight: Trigona
- Steering Clear of Security Blind Spots: What SOCs Need to Know
- Understanding the Kubernetes Security Triad: Image Scanning, Admission Controllers, and Runtime Security
 MQTT and M2M: Do You Know Who Owns Your Machine’s Data?
MQTT and M2M: Do You Know Who Owns Your Machine’s Data? Understanding the Kubernetes Security Triad: Image Scanning, Admission Controllers, and Runtime Security
Understanding the Kubernetes Security Triad: Image Scanning, Admission Controllers, and Runtime Security Ransomware Spotlight: Trigona
Ransomware Spotlight: Trigona Alexa and Google Home Devices can be Abused to Phish and Eavesdrop on Users, Research Finds
Alexa and Google Home Devices can be Abused to Phish and Eavesdrop on Users, Research Finds